Cyber Attacks on power grid: 10 power assets, Mumbai, Tamil Nadu ports came under RedEcho cyberattack | India Business News – Times of India
[ad_1]
Read More/Less
According to Christopher Ahlberg, CEO of Recorded Future, the Massachusetts-based enterprise security outfit that detected the intrusions, 10 Indian power sector assets and the Mumbai and Tamil Nadu’s VO Chidmabaranar ports came under attack.
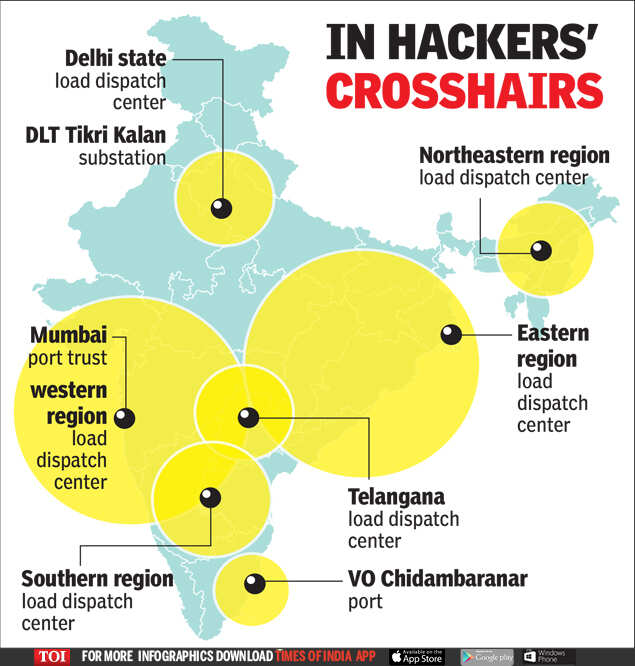
The power assets that came under attack were Delhi state load despatch centre, DTL Tikri Kalan substation in Delhi; Mumbai Port Trust, western regional load despatch centre In Maharashtra, NTPC’s Kudgi power plant and southern regional load despatch centre in Karnataka, VO Chidambarnar port in Tamil Nadu, Telengana load despatch centre, eastern regional load despatch centre in West Bengal load despatch centre and northeastern regional load despatch centre in Assam.
“Recorded Future observed through its network intelligence significant, high-volume, network traffic from Indian power sector assets to servers used by China-linked group RedEcho… The adversary infrastructure is still active and activity continues (even after Pangong pull-back announcement),” Ahlberg said in a presentation on the group’s findings on Thursday.
Charity Wright of Insikt, Recorded Future’s threat research group, said the location of targeted infrastructure covered the length and breadth of India’s geography as well as the demography.
A New York Times report had last Sunday blown the lid off on these intrusions, citing findings by Recorded Future. It raised doubt Chinese hackers may have caused the October 12 power outage in Mumbai as a warning against strong Indian pushback to PLA’s border transgressions in Ladakh.
On the power ministry’s statement that no installation was affected as safeguards were already in place, Wright said it showed the government responded to alerts. On power minister RK Singh blaming the Mumbai blackout on human error, Ahlberg said there was insufficient data to prove cyberattack caused the Mumbai blackout.
Targeting the Indian energy sector offers limited economic espionage opportunities. But the group believed “gathering future operational activity, pre-positioning destructive malware, as a warning/show of force during heightened bilateral tensions; and potential information operation to disturb Indian population” could be the possible objectives.
Ahlberg said RedEcho “has overlapping modus-operandi with several Chinese groups, including APT41 and Tonto Team,” the known cyber threat groups that take directions from established nation-states to carry out cyberattacks.
Wright said her group detected the intrusions using large-scale automated analytics and analysis. These included a combination of proactively identifying adversary infrastructure through server fingerprinting; identifying established sessions between the victim and adversary infrastructure through network traffic analysis; and enriching traffic analysis with proprietary data sources for victim identification.
This was the same methodology used to detect power sector intrusions in the European transmission control system, ENTSO-E.
[ad_2]
